Monday, December 20, 2010
Net Neutrality Legislation Passes in the US!
Wednesday, December 15, 2010
Monday, December 13, 2010
Inside Job
Is the global financial crisis an example of ethical egoism being unstable? Will it stabilize, or are the egos/interests of those involved too deeply associated with the legislation controlling the financial sector (specifically in the US).
Sunday, December 12, 2010
Has the Internet changed science?
Link is here: http://www.wisdomofwhores.com/wp-content/uploads/2010/12/Prospect_Big_data.pdf
Saturday, December 11, 2010
"Delete Facebook Account" search on Google
http://www.google.com/insights/search/#q=delete%20facebook%20account&cmpt=q
Any connection with the stats and facebook users being aware of privacy issues?
Thursday, December 9, 2010
The first truly honest privacy policy
Wednesday, December 8, 2010
Live updates of DDoS attacks against Visa/Mastercard
The technological and commercial skirmishes over WikiLeaks escalated into a full-blown online assault yesterday when, in a serious breach of internet security, a concerted online attack by activist supporters of WikiLeaks succeeded in disrupting MasterCard and Visa.
The acts were explicitly in "revenge" for the credit card companies' recent decisions to freeze all payments to the site, blaming illegal activity. Though it initially would acknowledge no more than "heavy traffic on its external corporate website", MasterCard was forced to admit last night that it had experienced "a service disruption to the MasterCard directory server", which banking sources said meant disruption throughout its global business.
Later, Visa's website was also inaccessible. A spokeswoman for Visa said the site was "experiencing heavier than normal traffic" and repeated attempts to load the Visa.com site was met without success.
Friday, December 3, 2010
CAN-SPAM Act in action
see what information is collected about you
http://betteradvertising.com/
New York professor installs camera in head
http://www.cnn.com/2010/US/12/02/new.york.camera.head/index.html?hpt=C1
There are obvious privacy concerns and university authorities require a cover over the lens when Bilal is teaching on campus.
Monday, November 29, 2010
WikiLeaks 9/11
Just want to share to people who have not realize this.
A brief summary of this is about 250000 highly confidential US diplomatic documents have been leaked out. I think this is related to our security topic.
http://wikileaks.org/
Sunday, November 28, 2010
Another side of technology and society
Thursday, November 25, 2010
Can you go to jail because of your tweets?
Tuesday, November 23, 2010
Judge Bars ‘Fair Use’ Defense in Xbox Modding Trial
Sunday, November 21, 2010
E-mail Privacy
Pin-less debit card
so starting from next summer, we maybe able to see this in Canada.
The basic idea of this card is to flash it above a detecting device and your items would be paid.
Personally, I think this idea is similar to those smart card idea. For example, in HK, we have the Octopus Card ( for more information go here: http://www.octopus.com.hk/home/en/index.html ) for many years already. Hence, I think Canada is a bit slow in using these technology.
Also, I kind of agree with the man in the news video that why they don't integrate this service into mobile devices? I am not 100% sure but I heard from my friends from Japan that they can do these similar transactions using their mobile devices. Maybe Joseph could show us some of these technology from Japan?
What do you guys think about this "new" pin-less debit card? Do you think it would be useful or effective at all?
Saturday, November 20, 2010
Old news but not everyone knows about it
Bell is one of the major ISPs over at the east coast and some people say that the government is trying to not let outside companies to try and compete (and improve) our internet infrastructure, bringing down competition.
http://www.crtc.gc.ca/eng/archive/2010/2010-802.htm
long read, tldr; for me.
But because of this, somewhere closer to us, Shaw has implemented a trial system of overage usage charges over at Edmonton.
http://www.dslreports.com/shownews/Shaw-Confirms-Plans-To-Charge-Per-Gig-Overages-11113
They are potentially bringing it to all the provinces they service.
What does that means to a lot of us? We're for sure gonna hit the cap and they're gonna milk money off consumers. They are overcharging at around $2 a gig, now by my experience of renting servers at data centers, I can buy like an extra block of 1TB of premium bandwidth for probably less than 20 bucks a month, I pay for a shared 100mbit unmetered hub at 35bucks with a server per month thats in Germany. The theoretical cap is about 4000GB/4TB which works out to be around 115Gigs per buck at a data center. Although its different because shaw has to send the service to you and do the infrastructure, the difference is HUGE.
With new streaming services to Canada like Netflix, we are also going to have a higher usage because of streaming HD content. So the upfront cost of Netflix is 8bucks or so, but by using it, we're also using up our bandwidth, which besides from the monthly cost, now has the overage usage cost, so we'll need to factor in the cost per movie we're streaming in the total cost of Netflix. I would probably be better off renting at Rogers than wasting my bandwidth streaming. It is also not a fair trade if you think about it. You are streaming thus you are not recording (well you can but lets say you cant). The amount of bandwidth used is not equal to the amount of data you get to store on your hard drive. In a sense it becomes a waste of bandwidth because you cant use that same portion of bandwidth again from playback because it is streamed.
Digital distribution platforms, getting more and more popular these days. Now I buy a lot of games off Steam and always delete/reinstall because of limited hard drive space. With the change, I will think twice as each game can cost me around 6 gigs of bandwidth (Black ops was 6 gigs). So besides the fact of the delete/reinstall cycle, the initial download will cost bandwidth, I will probably not bother buying anymore games online because It'll cost me another 10 bucks or so to download it. I personally do not see the future of digital distribution and DLC with implementation of these charges. Hell I'll stop my PS3 from auto-updating stuff as well. This may discourage mp3 buying sites like itunes, I'm not paying 99cents anymore, I'm paying a dollar and some cents plus tax. iTunes rental? nope not doing it 2.99 + atleast another 4 bucks for HD.
So all this may somehow tie into Net Neutrality in some ways. A question to ask is if I am getting charged per Gigabyte, is there a reason to prioritize say emails, because I am paying to use that bandwidth. Should ISPs still packet shape your transfers even though you are paying per gigabyte to use it?
so the tl:dr of all this is that the government is pretty backwards I guess.
Wednesday, November 17, 2010
International IT Security Issues: Operation Aurora and Stuxnet
Tuesday, November 16, 2010
Body Scanners Revealed
http://www.msnbc.msn.com/id/40218074/?gt1=43001
Video on new Facebook Messaging
Robots with ethics
Actors unhappy with Canada's Bill C-32
Actors believe the bill provides too much leeway for consumers. They are pushing for a levy to be added to hard drives and mp3 players in Canada. They are also against providing teachers with greater exemption with copy righted material used for education.
http://ca.news.yahoo.com/s/capress/101116/entertainment/actra_content
A really interesting article from the New Yorker
Saturday, November 13, 2010
Obama administration to target Internet privacy
Read more: http://www.vancouversun.com/technology/Obama+administration+target+Internet+privacy+report/3818787/story.html#ixzz15DjvKNXe
It's not "hypertext" as we know it...
Related to several topics from the censorship / online speech / internet addiction unit...
Sex, drugs more common in hyper-texting teens
By MIKE STOBBE, AP Medical Writer – Tue Nov 9, 4:09 am ET
ATLANTA – Teens who text 120 times a day or more — and there seems to be a lot of them — are more likely to have had sex or used alcohol and drugs than kids who don't send as many messages, according to provocative new research.
The study's authors aren't suggesting that "hyper-texting" leads to sex, drinking or drugs, but say it's startling to see an apparent link between excessive messaging and that kind of risky behavior.
...
http://news.yahoo.com/s/ap/20101109/ap_on_he_me/us_med_teens_texting
-----------------
I get the feeling a lot of people aren't going to notice the difference between correlation and causation...
Friday, November 12, 2010
Wednesday, November 24, 2010 is NATIONAL OPT-OUT DAY!
"...the government has done little to ensure that images taken by the devices are not saved. The TSA has asserted that the machines cannot store pictures, but security personnel at a courthouse in Florida were found to not only have saved images but shared them among colleagues in order to humiliate one of their co-workers."More information National Opt-Out Day: http://www.optoutday.com/ As stated on the site, the goal of National Opt Out Day is to "send a message to our lawmakers that we demand change. We have a right to privacy and buying a plane ticket should not mean that we're guilty until proven innocent. This day is needed because many people do not understand what they consent to when choosing to fly."
Facebook for the "privacy paranoid"
http://www.cnn.com/2010/TECH/social.media/11/12/facebook.superlogoff/index.html?eref=mrss_igoogle_cnn
Wednesday, November 10, 2010
Sask. man fights for Internet privacy after child porn conviction
Sask. man fights for Internet privacy after child porn conviction
Tuesday, November 9, 2010
Supreme Court Denies to Hear PATRIOT Act Challenge
http://www.csmonitor.com/USA/Justice/2010/1101/Supreme-Court-declines-to-hear-wrongly-accused-man-s-Patriot-Act-challenge
Sunday, November 7, 2010
Students' free speech rights on the move in the US
Friday, November 5, 2010
Meizu dead? Fake IPhone gone? No~no~
http://www.youtube.com/watch?v=RJL1Az16DEo
Hiphone 4 Hiphone 4GS Features:
• GSM Compatibility: Frequencies 850MHZ, 900MHZ, 1800MHZ, 1900MHZ
• Language: English, Spanish, French, Polish, Portuguese, Italian, German, Bahasa Melayu, Bahasa Indonesia, Czech, Dutch, Vietnamese, Russian, Bulgarian, Thai, Greek.
• Hiphone 4 Hiphone 4GS Screen: 3.3 inch, QVGA high vivid touch screen, 240*320 pixels
• Hiphone 4 Hiphone 4GS SIM Card Slots: 2 Card Slots
• Hiphone 4 Hiphone 4GS SIM Card Modes: Dual SIM open, Only SIM1 open, Only SIM2 open, Flight Mode
• Hiphone 4 Hiphone 4GS Security Settings: Phone lock, Auto Keypad lock, Change password
• Hiphone 4 Hiphone 4GS Camera: Dual camera. 2.0M pixel on the rear and self-capture camera on the front panel. Supports video-shoot, the duration depends on storage.
• Audio Player: Built-in
• Ring tone: supports MP3 audio record as ring tone
• User Profiles: General, Meeting, Outdoor, Indoor, Headset, Bluetooth
• Memory: Internal 89MB memory. TF Card Support (Up to 4GB in size)
• Vibration: Support
• Hiphone 4 GPRS Support: Browse WAP Website
• Messaging: SMS, MMS, Chat
• Games: Built-in Funny Games
• E-Book Reader: TXT
• JAVA Support: JAVA 2.0
• Bluetooth Support: Bluetooth 2.0
• Power Source: Standard Li-ion Battery
• Analog TV: YES
• Virtual keypad: Support
• Audio Output: Mini USB Port
• Shape: Bar Phone
• Hiphone 4 Dimensions:113 mm*59mm*13mm
Hiphone 4 Hiphone 4GS Specification:
• Multimedia:
- Camera, Image Viewer, Video Player, FM Radio, Sound recorder.
- Audio Player, Video recorder, E-book Reader, Analog TV
• File formats:
- Music: MP3, AMR, MID, WAV
- Image: BMP, GIF, JPG, BNG
- Video: 3GP, MP4
- E-Book: TXT
• TV Function:
- Type: Analog
- Options: Channel List, Manual input, My Channel, Channel Search, Search Area
- TV Record Format: 3GP
• Digital Still Camera:
- Image Quality: High, Normal, Low
- Camera Settings: Shuttle Sound, Delay Timer, Continuous Shot
- Other Options: White Balance, Scene Mode, Effect Settings, Set Frame
- EV: 4 steps (+2 to -2)
- Banding: 50Hz / 60Hz
• Video recorder:
- Video Record Format: 3GP
- Video Quality: Normal, Low, High
- Video Settings: Effects, White Balance, LED Highlight
- EV: 4 steps (+2 to -2)
- Banding: 50Hz / 60Hz
• Sound recorder setting:
- Storage: Phone, Memory Card
- File Format: AMR, WAV, AWB
- Sound quality: Low, High
• Audio Player:
- Formats: MP3, AMR, MID, WAV
- Options: Refresh list, Settings.
- Settings: Player Settings, Sound effects, Bluetooth Settings.
• FM Radio:
- Radio FM Tuner Frequency: 87.5MHz to 108MHz
- Background Play: ON, OFF
- Loudspeakers: ON, OFF
- Record Function: Yes
• Bluetooth:
- Type: MTK BT DEVICE
- Supported Service Profiles: Handsfree, Headset, SPP, DUN, OPP, FTP, A2DP, AVRCP, HID, BIP, SyncML service.
- Options: Power, Inquiry Audio Device, Remote Control, My Device, Active Devices, Settings
• Battery Life:
- Talk Time: Up to 3 hours
- Music Play: Up to 7 hours
- Stand By: Up to 120 hours
• Personal Organizer:
- Calendar, Tasks, World Clock, Synchronization, Phone sync.
Hiphone 4 Hiphone 4GS Package Content:
• 1 x F080 Mobile Phone
• 2 x Standard Li-ion Battery
• 1 x Travel Charger
• 1 x USB Cable
• 1 x User’s Manual (English)
• 1 x wired earphones with MIC and clip
Facebook Firing
http://ca.news.yahoo.com/s/03112010/73/bc-first-clear-facebook-firing-canada-occurs-pitt-meadows.html
Recommended Reading for Tuesday: "The Image Microsoft Doesn't Want You To See"

Thursday, November 4, 2010
Who's suing who? [Visualized]
Google for a Big Brother award in 2003
I find this article very interesting/entertaining about Google. Somehow it reminds me of the book 1984 by Orwell.
http://www.google-watch.org/bigbro.html
Wednesday, November 3, 2010
closing Digital Divide
Gaming can make a better world
Check it out here:
http://www.ted.com/talks/jane_mcgonigal_gaming_can_make_a_better_world.html
Tuesday, November 2, 2010
Facebook knows when you'll break up...
Monday, November 1, 2010
CPSC 490: CS Education (next term)
As I mentioned in class last time, next term I'm running a student directed seminar next term on CS education -- if you're finding an interest in what the public can and should know about CS, this is one of many issues we'll be talking about in the course! http://www.ugrad.cs.ubc.ca/~cs490/
Cheers,
Elizabeth
CPSC 490 coordinator
Humans Could Solve Digital Divide by Becoming the Network
The following is an example of a body to body network:
 The image states that data is streamed via "smart devices" using body to body networking
The image states that data is streamed via "smart devices" using body to body networkingFriends at the bar are able to watch impromptu performance in real-time without depending on mobile phone network.
More on the article...
http://thefrontline.v3.co.uk/2010/11/humans-could-so.html

"Firesheep allows easy hacking over open WiFi"
"Firesheep allows easy hacking over open WiFi."
Basically, a software developer has created a program called firesheep which uses unsecured wireless networks to hack into other users' Facebook and Twitter accounts. He also put the program on the internet for public download. The developer says he created the program in order to educate people about the dangers of using unsecured wireless networks. I'm not sure how ethical this was of him though. It seems dangerous to make a program like this available for public download.
Here is the link to the online article:
http://www.metronews.ca/vancouver/life/article/675035--firesheep-allows-easy-hacking-over-open-wifi
Sunday, October 31, 2010
Movies about government surveillance
More information about the movies:
The Conversation: http://www.imdb.com/title/tt0071360/
Enemy of the State: http://www.imdb.com/title/tt0120660/


Decision that Genes Shouldn't be Patentable in the U.S.
Friday, October 29, 2010
The 1440 Campaign Cycle
Thursday, October 28, 2010
some thought about ethical theories
Usage Based Billing
http://www.cbc.ca/technology/story/2010/10/28/crtc-usage-based-billing-internet.html
Sharing Too Much on Facebook Could Cost You
http://www.ctv.ca/generic/generated/static/business/article1770690.html
New FireFox extension makes logging in as others on unsecured wi-fi easy
Mother kills her baby over Farmville
Do you think people dieing over these games justifies the 'fun' it adds to the rest of the players who play them casually?
Here's the link: http://mashable.com/2010/10/28/farmville-murder-mother-baby/
Nader
Wednesday, October 27, 2010
Judge realizes: on the Internet, no one can tell you're a kid
Russia Crack Down on Spam
http://www.nytimes.com/2010/10/27/business/27spam.html?_r=1&ref=technology
Recommended Reading for Thursday / Tuesday: Info Security
Tuesday, October 26, 2010
Identity thieves crafty, prolific
Identity thieves crafty, prolific
Monday, October 25, 2010
What Stores Try To Cover Up
try as hard as they could to cover up any breaches to their database at the expense
of their customer's identity. It happens more often than you might think.
http://www.cbc.ca/marketplace/2010/whos_minding_the_store/main.html
http://www.cbc.ca/marketplace/2007/03/net_security.html
Sunday, October 24, 2010
What They Know: Interactive Infographic from WSJ
Really, Google?
Saturday, October 23, 2010
"MySpace moves against apps who share user data"
This caught my attention today: MySpace has started cracking down on app developers that share personal user data. This is in violation of MySpace's terms of use. I think this fits well with our current class topic of privacy and privacy invasion.
source: http://www.cnn.com/2010/TECH/web/10/23/myspace.leaks/index.html?eref=mrss_igoogle_cnn
Friday, October 22, 2010
What do you think about the new Facebook Groups?
Patenting Virtual Currency
“A method, comprising:receiving, at a server, a purchase order for virtual currency from a player, wherein the purchase order was made with legal currency, and wherein the virtual currency is usable within the context of a computer-implemented game;crediting an account of the player with virtual currency, wherein the virtual currency is not redeemable for legal currency;receiving a second purchase order for a virtual object within the context of the computer-implemented game from the player, wherein the second purchase order was made with virtual currency; and debiting the account of the player based on the second purchase order.”
More on:
http://techcrunch.com/2010/10/22/zynga-virtual-currency/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Techcrunch+%28TechCrunch%29
Steganography
http://gizmodo.com/5669317/student-hides-rick-astleys-song-in-college-paper
Thursday, October 21, 2010
Have anybody recently received Facebook scam email?
LEGO lost its trademark for its eight-stud brick design
It seems like even trademark has no expiry date, the court can take away the trademark.
http://www.lego.com/eng/info/default.asp?page=pressdetail&contentid=218350&countrycode=2057&yearcode=&archive=false
First surgery using robots only
Pushing the Bounds of Artistic Ownership
So can we say that British Heritage owns Stonehenge and all rights to it? They didn't really buy it. They didn't trade for it. They certainly didn't make it themselves. It's just that their distant, distant ancestors put some remarkably heavy slabs of stone in a particular place and left them there. Even if they didn't want it anymore, it's hardly as if they could just hide it in a bookshelf or stuff it in somebody's attic. But now it's there, and it's theirs, and it's popular, so they can take advantage of it. Seems a bit odd to me.
Wednesday, October 20, 2010
Hey Facebook, Here Are Some Other Companies You Can Bully Or Sue
Does this mean Facebook will also sue: travelbook, hotelbook, ebook, doctorsbook, racebook, tastebook etc...? :)
http://techcrunch.com/2010/08/26/facebook-placebook-teachbook/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed:+Techcrunch+(TechCrunch)
Tuesday, October 19, 2010
"Google accidentally mapped much more than addresses, says privacy boss"
http://www.thestar.com/business/article/877850--google-accidentally-mapped-much-more-than-addresses-says-privacy-boss
Entrepreneur Takes On Apple And Wins $625 Million Read more: http://www.businessinsider.com/entrepreneur-takes-on-apple-and-wins-625mm-2010-10#ixzz12
Google, Facebook To Microsoft’s Paul Allen: Your Argument Is Invalid!
http://techcrunch.com/2010/08/27/paul-allen-google-faceboo/?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Techcrunch+%28TechCrunch%29
""Patent #682 “Alerting Users to Items of Current Interest.
“Defendant Facebook has infringed and continues to infringe one or more claims of the ’682 patent. Facebook is liable for infringing the ’682 patent under 35 U.S.C. § 271 by making and using websites and associated hardware and software to provide alerts that information is of current interest to a user as claimed in the patent.”“Defendant Google has infringed and continues to infringe one or more claims of the ’682 patent. Google is liable for infringing the ’682 patent under 35 U.S.C. § 271 by making and using websites and associated hardware and software to provide alerts that information is of current interest to a user as claimed in the patent.”"
Monday, October 18, 2010
HyperMac stops selling magsafe connectors
Sunday, October 17, 2010
Court says University sanction over Facebook postings violated Charter
Map of Online Communities - updated 2010!
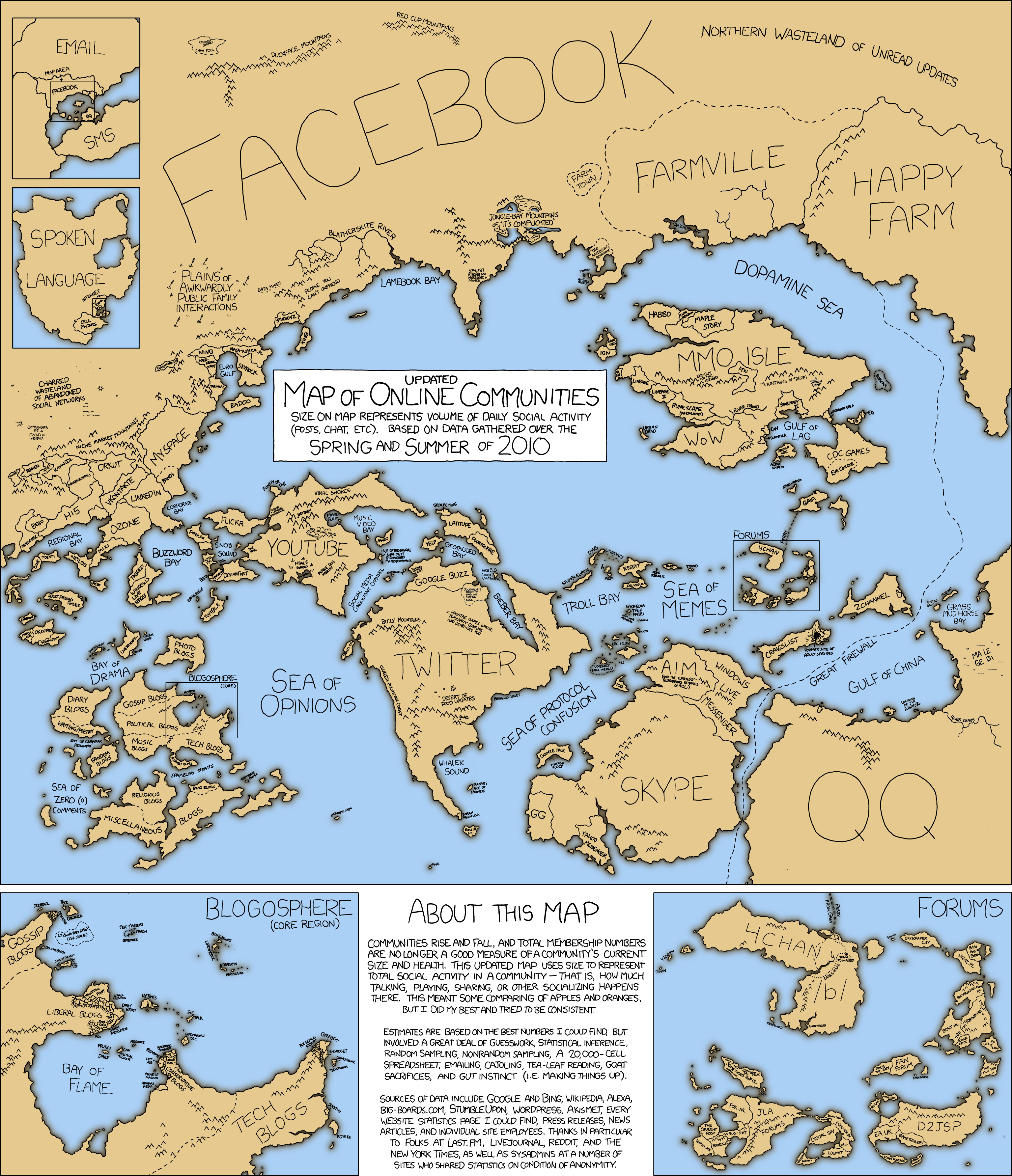
I remember seeing something like this map a long time ago, and I just stumbled upon this brand new updated version from summer 2010! Enjoy. This map is based on activity levels, as supposed to number of users, (which would probably explain why Farmville is so friggin huge, it's probably used for hours on end by many people, while twitter is only accessed maybe 3 times a day for an average user? Same with 4chan's prominence among forums, maybe it's the type of thing people spend long hours on? internet addiction?) You also have to wonder about possible bias towards North American / English language activities (although there is China's "QQ" messenger, and "Euro Gulf")
My Highlights:
• Shaq in the Twitter territory
• "Former site of adult services" in Craigslist territory (crater)
• Myspace's huge importance for bands, music videos' prominence on Youtube
• "Web 3.0 (under construction)"
• "Sea of Protocol Confusion"
• Sarah Palin USA's proximity to Russia
• "Catbus Route" on the 4chan island
• Bieber Bay!
Amazing.
Saturday, October 16, 2010
New US Internet Censorship bill
This article is even more relevant to our fellow American 430'ers - but can touch us all as we all use youtube and similar services on a regular basis.. This bill could effectively overturn the recent supreme court decision that prevented Viacom from removing clips of their shows from youtube.com...
"Stop the Internet Blacklist
By David Segal and Aaron Swartz
When it really matters to them, Congressmembers can come together -- with a panache and wry wit you didn't know they had. As banned books week gets underway, and President Obama admonishes oppressive regimes for their censorship of the Internet, a group of powerful Senators -- Republicans and Democrats alike -- have signed onto a bill that would vastly expand the government's power to censor the Internet.
The Combating Online Infringement and Counterfeits Act (COICA) was introduced just one week ago, but it's greased and ready to move, with a hearing in front of the Judiciary Committee this Thursday. If people don't speak out, US citizens could soon find themselves joining Iranians and Chinese in being blocked from accessing broad chunks of the public Internet.
COICA creates two blacklists of Internet domain names. Courts could add sites to the first list; the Attorney General would have control over the second. Internet service providers and others (everyone from Comcast to PayPal to Google AdSense) would be required to block any domains on the first list. They would also receive immunity (and presumably the good favor of the government) if they block domains on the second list.
The lists are for sites "dedicated to infringing activity," but that's defined very broadly -- any domain name where counterfeit goods or copyrighted material are "central to the activity of the Internet site" could be blocked.
One example of what this means in practice: sites like YouTube could be censored in the US. Copyright holders like Viacom often argue copyrighted material is central to the activity of YouTube, but under current US law, YouTube is perfectly legal as long as they take down copyrighted material when they're informed about it -- which is why Viacom lost to YouTube in court.
But if COICA passes, Viacom wouldn't even need to prove YouTube is doing anything illegal to get it shut down -- as long as they can persuade the courts that enough other people are using it for copyright infringement, the whole site could be censored.
Perhaps even more disturbing: Even if Viacom couldn't get a court to compel censorship of a YouTube or a similar site, the DOJ could put it on the second blacklist and encourage ISPs to block it even without a court order. (ISPs have ample reason to abide the will of the powerful DOJ, even if the law doesn't formally require them to do so.)"

